- November 6, 2017
- Posted by: Syed Shujaat
- Category: Uncategorized
Windows Server Event Logs
who restarted windows server
log in to the server. The below steps work on Windows Server 2008, 2008 R2 and Server 2012 R2. Launch the Event Viewer (type eventvwr in run). In the event viewer console expand Windows Logs. Click on System and in the right pane click Filter Current Log.
In the Filter Current log box, type 1074 as the event ID. This will filter the events and you will see events only with ID 1074.
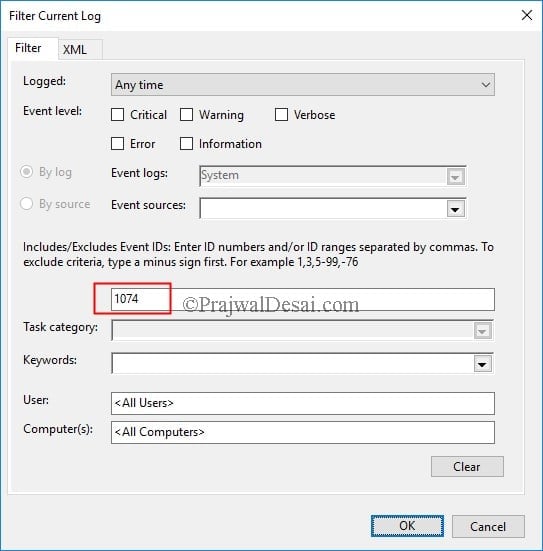
The process C:\Windows\System32\RuntimeBroker.exe (CORPAD) has initiated the restart of computer CORPAD on behalf of user PRAJWAL\sccmadmin for the following reason: Other (Unplanned)
Reason Code: 0x5000000
Shutdown Type: restart
Who Logged In
You’re looking for events with the event ID 4624—these represent successful login events. You can see details about a selected event in the bottom part of that middle-pane, but you can also double-click an event see its details in their own window.


Reboot/Shutdown, force Shutdown Event Logs :
- Event ID 1074: “The process X has initiated the restart / shutdown of computer on behalf of user Y for the following reason: Z.” Indicates that an application or a user initiated a restart or shutdown.
- Event ID 1076: “The reason supplied by user X for the last unexpected shutdown of this computer is: Y.” Records when the first user with shutdown privileges logs on to the computer after an unexpected restart or shutdown and supplies a reason for the occurrence.
- Event ID 6005: “The event log service was started.” This is synonymous to system startup.
- Event ID 6006: “The event log service was stopped.” This is synonymous to system shutdown.
- Event ID 6008: “The previous system shutdown was unexpected.” Records that the system started after it was not shut down properly.
- Event ID 6009: Indicates the Windows product name, version, build number, service pack number, and operating system type detected at boot time.
- Event ID 6013: Displays the uptime of the computer. There is no TechNet page for this id.
- Event ID 7036 telling you that various services “entered the stopped state.” As the machine starts up again, you will see more 7036s announcing that services are entering the running state.
Logon Type:
This is a valuable piece of information as it tells you HOW the user just logged on:
|
Logon Type
|
Description
|
| 2 | Interactive (logon at keyboard and screen of system) |
| 3 | Network (i.e. connection to shared folder on this computer from elsewhere on network) |
| 4 | Batch (i.e. scheduled task) |
| 5 | Service (Service startup) |
| 7 | Unlock (i.e. unnattended workstation with password protected screen saver) |
| 8 | NetworkCleartext (Logon with credentials sent in the clear text. Most often indicates a logon to IIS with “basic authentication”) See this article for more information. |
| 9 | NewCredentials such as with RunAs or mapping a network drive with alternate credentials. This logon type does not seem to show up in any events. If you want to track users attempting to logon with alternate credentials see 4648. |
| 10 | RemoteInteractive (Terminal Services, Remote Desktop or Remote Assistance) |
| 11 | CachedInteractive (logon with cached domain credentials such as when logging on to a laptop when away from the network) |
Impersonation Level: (Win2012 only)
From MSDN
| Anonymous | Anonymous COM impersonation level that hides the identity of the caller. Calls to WMI may fail with this impersonation level. |
| Default | Default impersonation. |
| Delegate | Delegate-level COM impersonation level that allows objects to permit other objects to use the credentials of the caller. This level, which will work with WMI calls but may constitute an unnecessary security risk, is supported only under Windows 2000. |
| Identify | Identify-level COM impersonation level that allows objects to query the credentials of the caller. Calls to WMI may fail with this impersonation level. |
| Impersonate | Impersonate-level COM impersonation level that allows objects to use the credentials of the caller. This is the recommended impersonation level for WMI calls. |
New Logon:
The user who just logged on is identified by the Account Name and Account Domain. You can determine whether the account is local or domain by comparing the Account Domain to the computer name. If they match, the account is a local account on that system, otherwise a domain account.
- Security ID: the SID of the account
- Account Name: Logon name of the account
- Account Domain: Domain name of the account (pre-Win2k domain name)
- Logon ID: a semi-unique (unique between reboots) number that identifies the logon session just initiated. Any events logged subsequently during this logon session will report the same Logon ID through to the logoff event 4647 or 4634.
- Logon GUID: Supposedly you should be able to correlate logon events on this computer with corresonding authentication events on the domain controller using this GUID. Such as linking 4624 on the member computer to 4769 on the DC. But the GUIDs do not match between logon events on member computers and the authentication events on the domain controller.
Process Information:
Leave a Reply
You must be logged in to post a comment.