- June 25, 2018
- Posted by: Syed Shujaat
- Category: Uncategorized
Windows 10 RDP CredSSP Encryption Oracle Remediation Error Fix
Just a couple of days ago, the cumulative updates were released below for Windows 10 and Server 2016, etc. These cumulative updates include the fix for the CredSSP encryption vulnerability.
May 8, 2018 – KB4103721 (OS Build 1803)
May 8, 2018 – KB4103727 (OS Build 1709)
May 8, 2018 – KB4103731 (OS Build 1703)
May 8, 2018 – KB4103723 (OS Build 1609 & Server 2016)
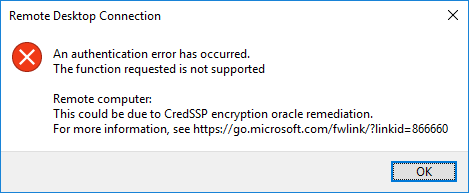
Once you have installed the patch on a “vulnerable” workstation and attempt to connect to an unpatched server, you will see the following error message that happens after you type in your password to authenticate to the RDP session.
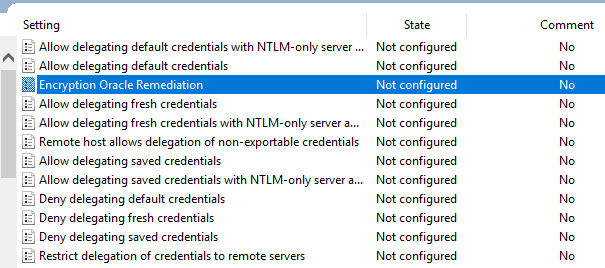
There is a local policy setting that is added with the installed security updates. You can find this at Computer Configuration >> Administrative Templates >> System >> Credentials Delegation >> Encryption Oracle Remediation. By default this is set to Not configured.
To Fix the issue as a workaround, set the policy to Enabled and set the Protection Level to Vulnerable.
***Note*** – This is not recommended by Microsoft, as making sure both the client and server is patched is best practice. However, setting the policy to Vulnerable allows your workstation to now connect to the remote desktop session that was previously blocked by the mitigation.
CredSSP Encryption Oracle Remediation Registry Setting
Alternatively, you can set this policy setting via the registry and a reboot.
- [HKEY_LOCAL_MACHINE\SOFTWA
RE\Microso ft\Windows \CurrentVe rsion\Poli cies\Syste m\CredSSP\ Parameters ] “AllowEncryptionOracle”=dw ord:000000 02
Leave a Reply
You must be logged in to post a comment.