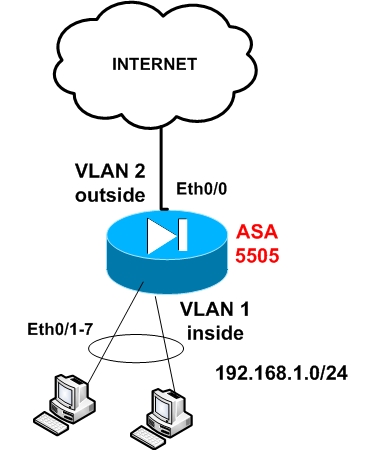
Step1: Configure the internal interface vlan
ASA5505(config)# interface Vlan 1
ASA5505(config-if)# nameif inside
ASA5505(config-if)# security-level 100
ASA5505(config-if)# ip address 192.168.1.1 255.255.255.0
ASA5505(config-if)# no shut
Step 2: Configure the external interface vlan (connected to Internet)
ASA5505(config)# interface Vlan 2
ASA5505(config-if)# nameif outside
ASA5505(config-if)# security-level 0
ASA5505(config-if)# ip address 200.200.200.1 255.255.255.0
ASA5505(config-if)# no shut
Step 3: Assign Ethernet 0/0 to Vlan 2
ASA5505(config)# interface Ethernet0/0
ASA5505(config-if)# switchport access vlan 2
ASA5505(config-if)# no shut
Step 4: Enable the rest interfaces with no shut
ASA5505(config)# interface Ethernet0/1
ASA5505(config-if)# no shut
Step 5: Configure PAT on the outside interface
ASA5505(config)# global (outside) 1 interface
ASA5505(config)# nat (inside) 1 0.0.0.0 0.0.0.0
UPDATE for ASA Version 8.3 and later
From March 2010, Cisco announced the new Cisco ASA software version 8.3. This version introduced several important configuration changes, especially on the NAT/PAT mechanism. The “global” command is no longer supported. NAT (static and dynamic) and PAT are configured under network objects. The PAT configuration below is for ASA 8.3 and later:
object network obj_any
subnet 0.0.0.0 0.0.0.0
nat (inside,outside) dynamic interface
Step 6: Configure default route towards the ISP (assume default gateway is 200.200.200.2)
ASA5505(config)# route outside 0.0.0.0 0.0.0.0 200.200.200.2 1
The above steps are the absolutely necessary steps you need to configure for making the appliance operational. Of course there are much more configuration details that you need to implement in order to enhance the security and functionality of your appliance, such as Access Control Lists, Static NAT, DHCP, DMZ zones, authentication etc.
Steps to upgrade your Cisco IOS
Install TFTP client on the machine is on the same network as of ASA Ethernet 0/1 – inside network. Download Cisco ASA upgrade/ASDMA files and associate your TFTP default link to the folder containing files.
Connect to TFTP to upload your file by following CLI command
ciscoasa(config)# copy tftp: disk0:
Address or name of remote host [127.0.0.1]?
Source filename [asa917-32-k8.spa]?
Destination filename [asa917-32-k8.spa]?
Accessing tftp://192.168.1.200/asa917-32-k8.bin…!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
27426816 bytes copied in 34.470 secs (806671 bytes/sec)
ciscoasa(config)# copy tftp: flash:
Address or name of remote host [192.168.1.200]?
Source filename [asa917-32-k8.bin]? asdm-7122.bin
Destination filename [asdm-7122.bin]?
Accessing tftp://192.168.1.200/asdm-7122.bin…!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Writing file disk0:/asa917-32-k8.bin…
33696792 bytes copied in 41.620 secs (821872 bytes/sec)
ciscoasa(config)#
ciscoasa(config)# asdm image flash:asdm-7122.bin
ciscoasa(config)# boot system flash:asa917-32-k8.bin
INFO: Converting flash:asa917-32-k8.bin to disk0:/asa917-32-k8.bin
ciscoasa#reload ! restart your machine
ciscoasa(config)# http server enable
ciscoasa(config)# http 0.0.0.0 0.0.0.0 inside
ciscoasa(config)# copy run start